Understanding School Cybersecurity: How to Start & Stay Safe
If you’ve been following Avertere's blogs, you likely know a thing or two about online threats aimed at educational settings like schools. But,...
2 min read
Jack Britton
Aug 16, 2023 8:37:50 PM

Greetings, K12 School champions! Our recent explorations, “How to Spot Cyber Threats that Could Harm Schools” and “Cyber Threats to Edu Cloud Platforms: Google Workspace,” offered a deep dive into the MITRE ATT&CK framework. Think of it as our digital detective toolkit to understand those pesky cyber bullies. Now, let’s delve into MITRE D3FEND - our digital shield against those virtual threats. Curious? Let’s jump in!
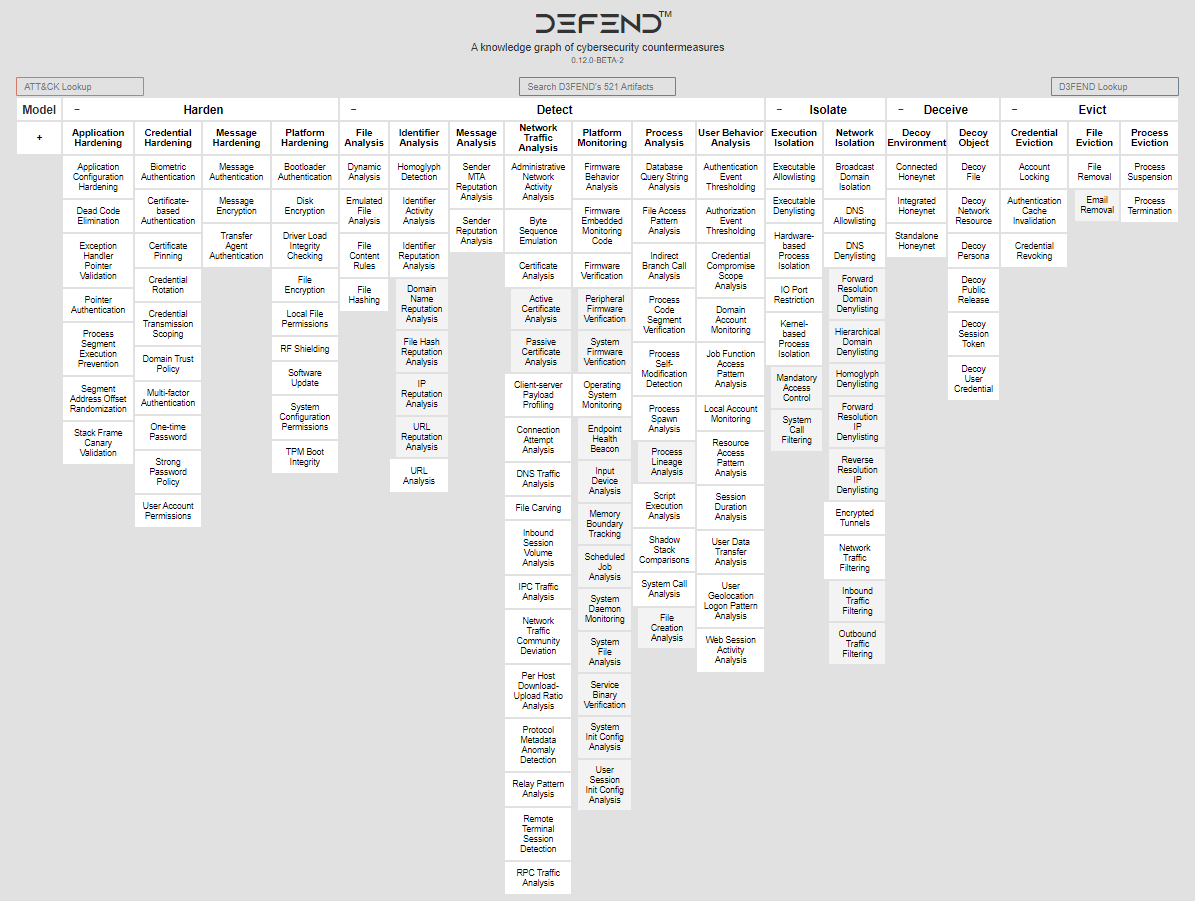
Ever wished for a manual that not only points out the sneaky digital threats but also suggests the best protective measures for our school systems? That's what MITRE D3FEND offers. It's a comprehensive guide to cybersecurity defenses, laid out for clarity and ease.
For educators and tech facilitators aiming to create safe digital environments, D3FEND is a game-changer. With insights from over 500 countermeasure patents, this framework lets you connect the dots from potential cyber threats to actionable defense strategies. So, when you're considering a new software or digital tool for your school, you've got a reference to check its safety credentials.
With this intel in hand, it's time to find our digital shields!
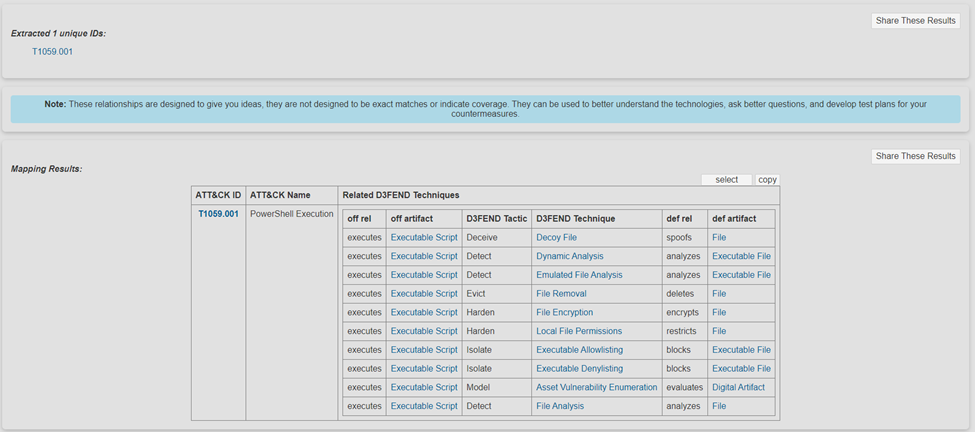
Look at the "off rel" column, first row, from the beginning to the end. If someone bad runs a PowerShell script, it leaves a artifact called "Executable Script." To trick this bad person, we can make decoy files. These decoy files can send us warnings and help us spot when they're trying to steal using PowerShell Scripts.
Try selecting the D3FEND Technique, like "Decoy File"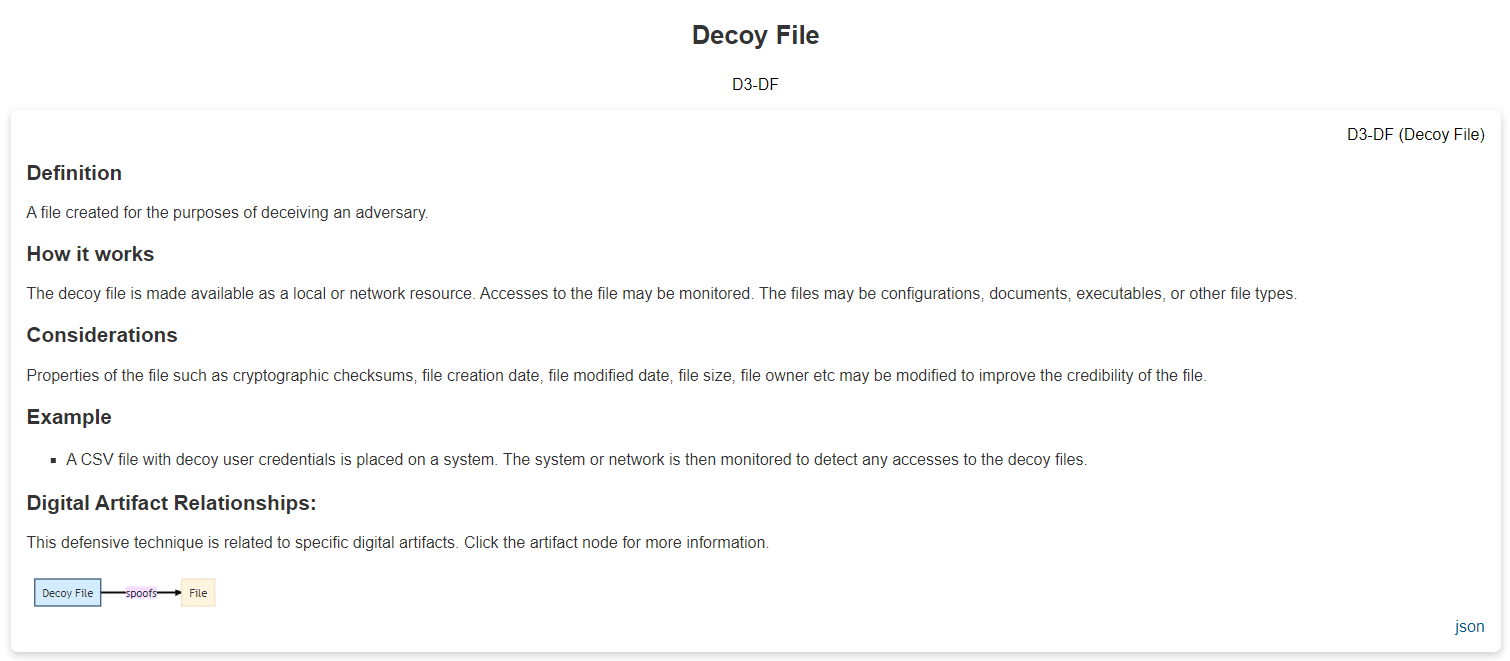
To draw an analogy:
When combined, these tools ensure our schools' digital environments are safe, secure, and optimized for education. After all, our students deserve nothing less than the best, both offline and online.
Was this guide helpful? If so, give us a shoutout! At Avertere, we’re passionate about elevating K12 digital safety. Do share your insights, suggestions, and let's make our digital classrooms safer together! 🍎💻🛡

If you’ve been following Avertere's blogs, you likely know a thing or two about online threats aimed at educational settings like schools. But,...

Greetings, K12 School champions! Our recent explorations, “How to Spot Cyber Threats that Could Harm Schools” and “Cyber Threats to Edu Cloud...

In a previous blog, we delved into identifying cyber threats to schools and how they cause impact using MITRE ATT&CK. Today, we narrow down our focus...