Understanding School Cybersecurity: How to Start & Stay Safe
If you’ve been following Avertere's blogs, you likely know a thing or two about online threats aimed at educational settings like schools. But,...
2 min read
Jack Britton
Aug 8, 2023 2:44:07 PM


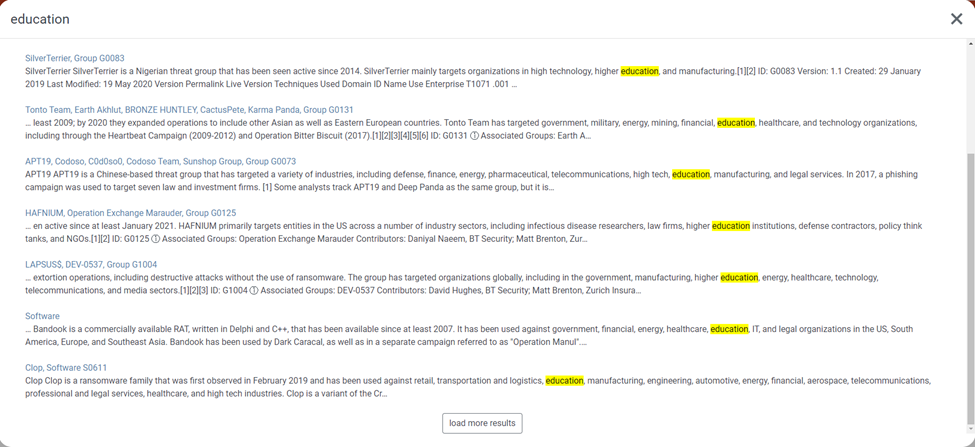
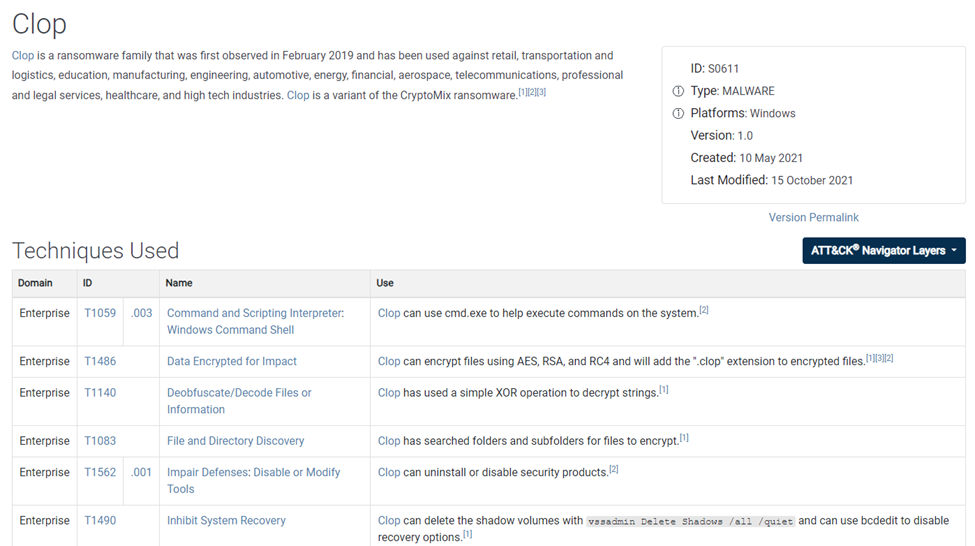
In a previous blog, we delved into identifying cyber threats to schools and how they cause impact using MITRE ATT&CK. Today, we narrow down our focus to understanding how adversary groups attack cloud-based platforms (Google Workspace), particularly in the educational sector.
If you missed our previous article, "How to Spot Cyber Threats that Could Harm Schools", it's beneficial to start there for a broad perspective. This piece will give a step-by-step guide with visuals for clarity.
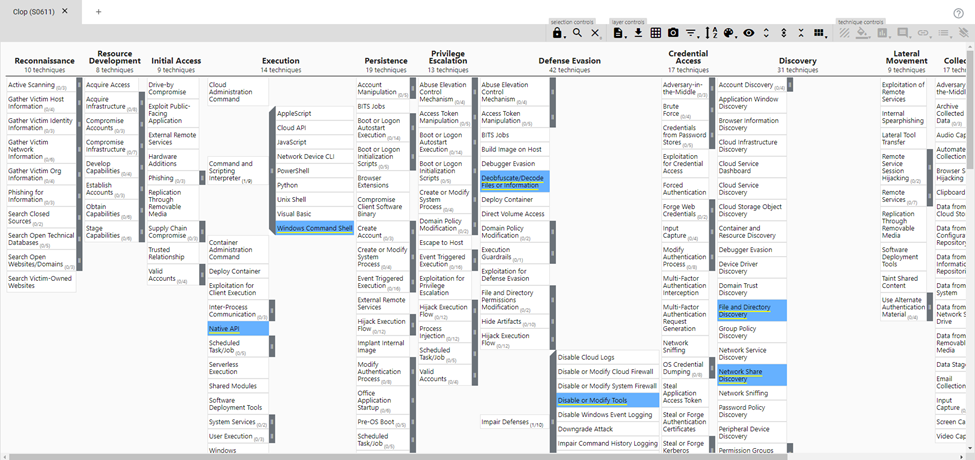
Tailor to Google Workspace: For institutions using Google Workspace, filter the results. On the top right, there's an icon (see red arrow). Click on the filter icon and deselect all but "Google Workspace". There should only be one blue square and that is the one next to Google Workspace.
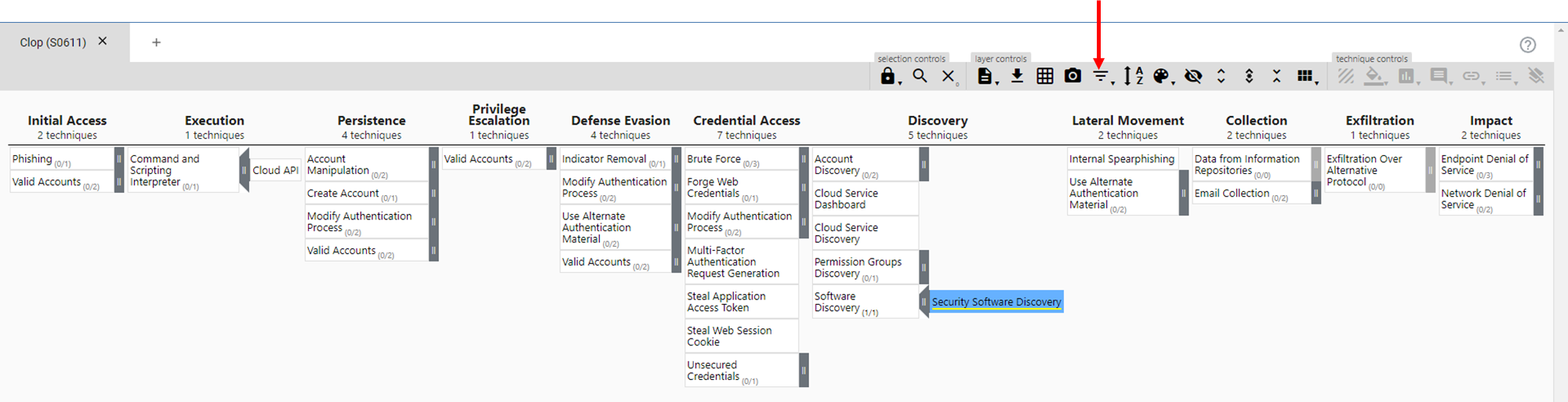
The outcome? You'll see precisely how Clop and others adversaries first gains initial access to an organization that uses Google Workspace and then the sequence of techniques they deploy for maximum damage.
For schools to effectively defend against such threats, here are some questions to consider:
The MITRE ATT&CK framework, when harnessed effectively, provides educational institutions a clearer picture of potential threats, particularly when targeting specific platforms like Google Workspace. By leveraging this knowledge, K12 organizations can build stronger, tailored defenses.
Avertere offers no-cost evaluations for K12 institutions, assessing potential risks. Interested? Contact Us for assistance.
Found this piece insightful? Share it within the K12 community and engage with us. Drop your questions or comments below.

If you’ve been following Avertere's blogs, you likely know a thing or two about online threats aimed at educational settings like schools. But,...

Greetings, K12 School champions! Our recent explorations, “How to Spot Cyber Threats that Could Harm Schools” and “Cyber Threats to Edu Cloud...

In a previous blog, we delved into identifying cyber threats to schools and how they cause impact using MITRE ATT&CK. Today, we narrow down our focus...