Understanding School Cybersecurity: How to Start & Stay Safe
If you’ve been following Avertere's blogs, you likely know a thing or two about online threats aimed at educational settings like schools. But,...


Who is trying to break into your school's digital space, and why should you care? Cyber criminals are individuals who use the digital world for malicious and personal profit. In our case, we're focusing on those who aim at the education sector, possibly disrupting school services and affecting students, teachers, and administrators. But why is this important? Because knowing who these cyber villains are helps us protect ourselves more effectively. In this blog, we're going to explore how we can safeguard our schools. And don't worry, we'll soon cover how you can protect your personal data at home in case it gets stolen from a school's system. Ready to dive in?
Have you ever wished for a guidebook on how cyber baddies do their dirty work? That's exactly what MITRE ATT&CK is! It's a comprehensive resource that helps cybersecurity pros understand how cyber criminals plan and execute their attacks.
Just like a big book of villainous tactics, it lists all the sneaky tricks hackers use to break into systems, move around unnoticed, and accomplish their evil deeds. This could involve deceptive emails (phishing), planting harmful software (malware), and stealing data, among other things.
ATT&CK is an awesome tool that gives cybersecurity experts a common language to talk about cyber threats. Think of it like a big library of hacking tactics that can be used to fight back, spot signs of a break-in, and up our digital defense game. By learning the enemy's playbook, we can plan better strategies to keep our systems safe.
Ready to start? Visit: https://attack.mitre.org/
First, click the "Search" icon at the top right-hand corner of the website and type in "Education." What you'll see should look something like this: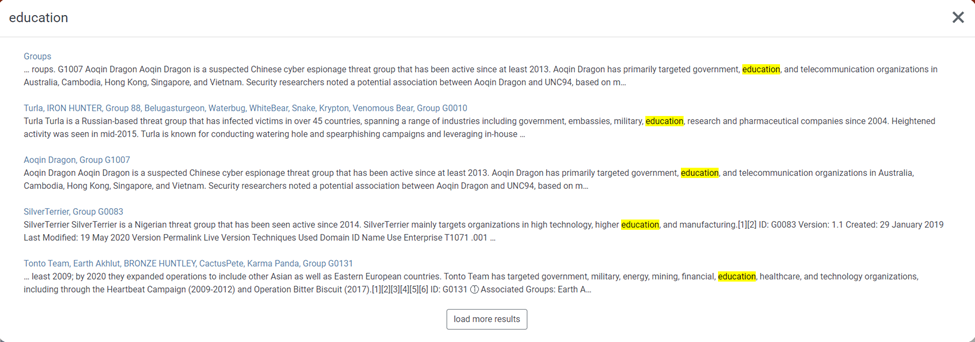
By clicking on "Groups," you'll see a list of all the cyber bad guys who love to target education. Quick tip: use CTRL+F and search "Education" to easily spot them. One notorious group you should look at is the infamous LAPSUS$ gang, also known as Group G1004.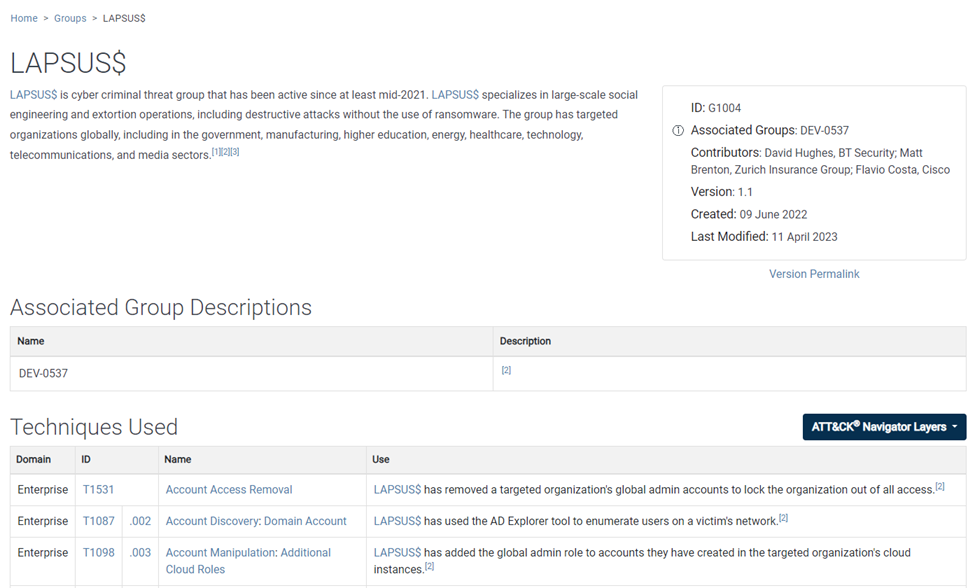
On the Group page, you'll find all the tools and tricks these cyber bullies use to gain an upper hand. You'll also see what software they usually use. Knowing this information is like having a secret playbook to plan your defense strategies. Here are some key questions to ask:
Knowing who the digital bad guys targeting your industry are and how they work is crucial in making the right decisions about your cybersecurity investments. Was this blog helpful? Any questions? If you want to learn more in a free workshop, just contact Avertere on our 'Contact Us' page. We're here to help you stay safe in the digital world.

If you’ve been following Avertere's blogs, you likely know a thing or two about online threats aimed at educational settings like schools. But,...

Greetings, K12 School champions! Our recent explorations, “How to Spot Cyber Threats that Could Harm Schools” and “Cyber Threats to Edu Cloud...

In a previous blog, we delved into identifying cyber threats to schools and how they cause impact using MITRE ATT&CK. Today, we narrow down our focus...