Understanding School Cybersecurity: How to Start & Stay Safe
If you’ve been following Avertere's blogs, you likely know a thing or two about online threats aimed at educational settings like schools. But,...
3 min read
Jack Britton
Jan 10, 2023 5:46:49 PM
.png)
When a cyber incident occurs, administrators and faculty members rush to respond. In post-recovery, Cybersecurity is a high priority, and the leadership decides to hire a Cybersecurity firm that performs a "Risk Assessment" based on a Cybersecurity Framework. They offer a prioritization of risk-reduction "Activities" or "Best Practices" and a maturity model to measure success over time.
By completing these activities and maturing as an organization, the K12 school will naturally be more resilient to Cyber threats, right?
There is often an overlooked piece of the puzzle: Who will do the work? When formulating a cybersecurity strategy, consider these five tips to ensure resiliency to cyber threats:
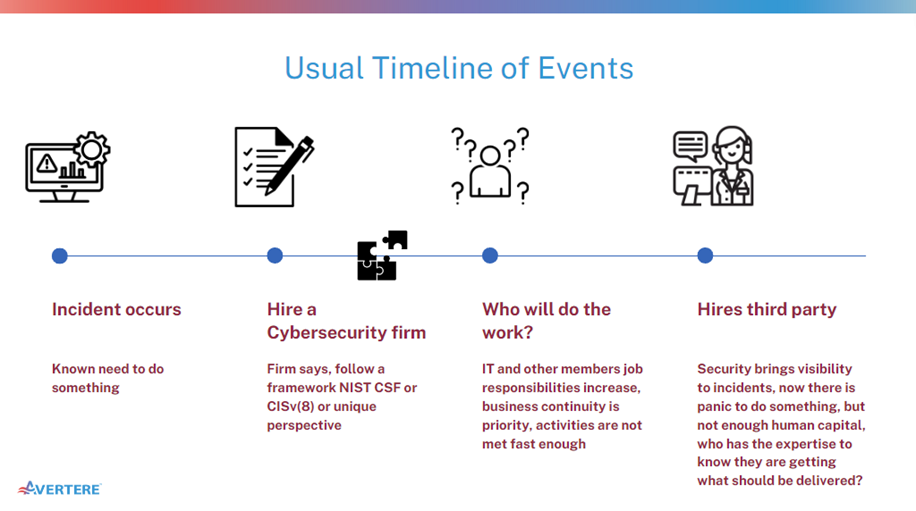
It is natural for many K12 organizations to assign the IT department the responsibility of performing Cybersecurity work. After all, it's Information Technology we are talking about, right? The IT department's priority is business continuity, and by taking responsibility for security, business continuity becomes a conflict of interest or is a secondary priority.
In other words, that is like hiring a handyperson to do electrical work. The handyperson can do the job for the money. Still, the more complex the work becomes, the greater probability that a not-to-code and potentially dangerous electrical condition may be created. They are different disciplines, and they require different training.
By adopting a common language for "Who will do the work," administrators and faculty members can align human resource hiring practices with cybersecurity priorities. Furthermore, internal staff will have a reference of the knowledge, skillsets, and abilities required to perform the Cybersecurity "activities" or "work." Budget requirements for a workforce will be more predictable and descriptive than previously and in alignment with the Cybersecurity program maturity.
Adopting a framework to describe your Cybersecurity workforce creates a common language for stakeholders, HR, IT Department, and the Security department to explain who will do the work. Amongst professionals in the cybersecurity industry, it is not uncommon for a meme to be posted on LinkedIn regarding a job post that requires 20 years of experience and several different disciplines of certifications for a cyber analyst role.
This is a clear indicator that the company has Cybersecurity "activities" or "work" they need to accomplish, but they don't understand the workforce requirements. By adopting a Cyber Workforce framework and mapping it to the prioritized Cybersecurity activities, the needs of today and the years following become clearer.
You have a Security Department - that is outstanding! Do you have a high turnover? Are your internal surveys indicating that security professionals leave because they feel there is no career progression?
Career progression requires training which requires budget planning and mapping the skillsets and abilities needed to meet the higher maturity or more complex risk reduction activities—leveraging a Cybersecurity workforce framework maps activities to the knowledge, skills, and abilities required to perform the work. Thankfully, training - and where to get the training - is an opportunity to plan for budget and career progression.
When an organization needs to meet Cybersecurity objectives but needs help solving the workforce problem, the solution is often to buy more products. Adding additional software or product to the environment increases the need for maintenance, operations, and the overall threat landscape. Essentially, there is more opportunity for a bad guy to take advantage of if more software enables the environment's access.
Organizations often hire third-party vendors to meet their Cybersecurity objectives. An investment in third-party managed security service providers (MSSPs) is a good idea if it makes good business sense and feels like a partnership. However, consider third-party risk.
For example, in a recent real-world incident, a third party used by many in the higher and lower education sector was breached, resulting in them becoming victims of ransomware. It impacted them and their customers significantly and led to a Class Action lawsuit.
In this scenario, it is possible the schools had some level of indemnification per their contract with the third party. However, the damage caused may not have been fully covered through their liability or cyber insurance. The school was still responsible for the data breach, regardless of whether a third party was hosting it. To achieve coverage, the school had to prove due diligence and due care in alignment with the insurance policy's fine print.
The events described here may not apply to all, but it is a common theme amongst most K12 districts. Please share your experiences in the comments below.
By now, you understand the value of adopting a Cybersecurity Workforce framework and mapping human capital requirements with the cybersecurity risk reduction priorities.
Avertere is a complete Cybersecurity consulting and services firm dedicated solely to student and administrative safety within the education sector. We want to bring security to all schools and converge physical and Cybersecurity services on behalf of the education sector, so our teachers can focus on teaching.
Avertere can be your partner regardless of where you are in your journey. Please follow us on LinkedIn or contact us here at avertere.com.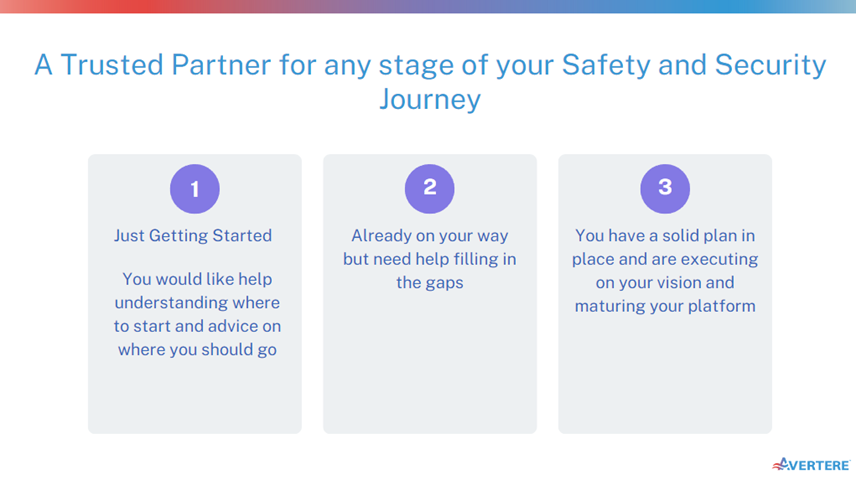
See our offerings here:


If you’ve been following Avertere's blogs, you likely know a thing or two about online threats aimed at educational settings like schools. But,...

Greetings, K12 School champions! Our recent explorations, “How to Spot Cyber Threats that Could Harm Schools” and “Cyber Threats to Edu Cloud...

In a previous blog, we delved into identifying cyber threats to schools and how they cause impact using MITRE ATT&CK. Today, we narrow down our focus...